Integrate with MOSIP e-Signet
Description
Pre-requisites
Steps
Configure OpenG2P as a partner on MOSIP
Configure OpenG2P as relying party on e-Signet
Using PMS API
post
Body
idstringOptional
versionstringOptional
requesttimestring · date-timeOptional
metadataobjectOptional
Responses
200
OK
application/json
idstringOptional
versionstringOptional
responsetimestring · date-timeOptional
metadataobjectOptional
post
/oidc/client200
OK
Using e-Signet API
post
Body
requestTimestringOptional
Responses
200
OK
application/json
responseTimestringOptional
post
/client-mgmt/oidc-client200
OK
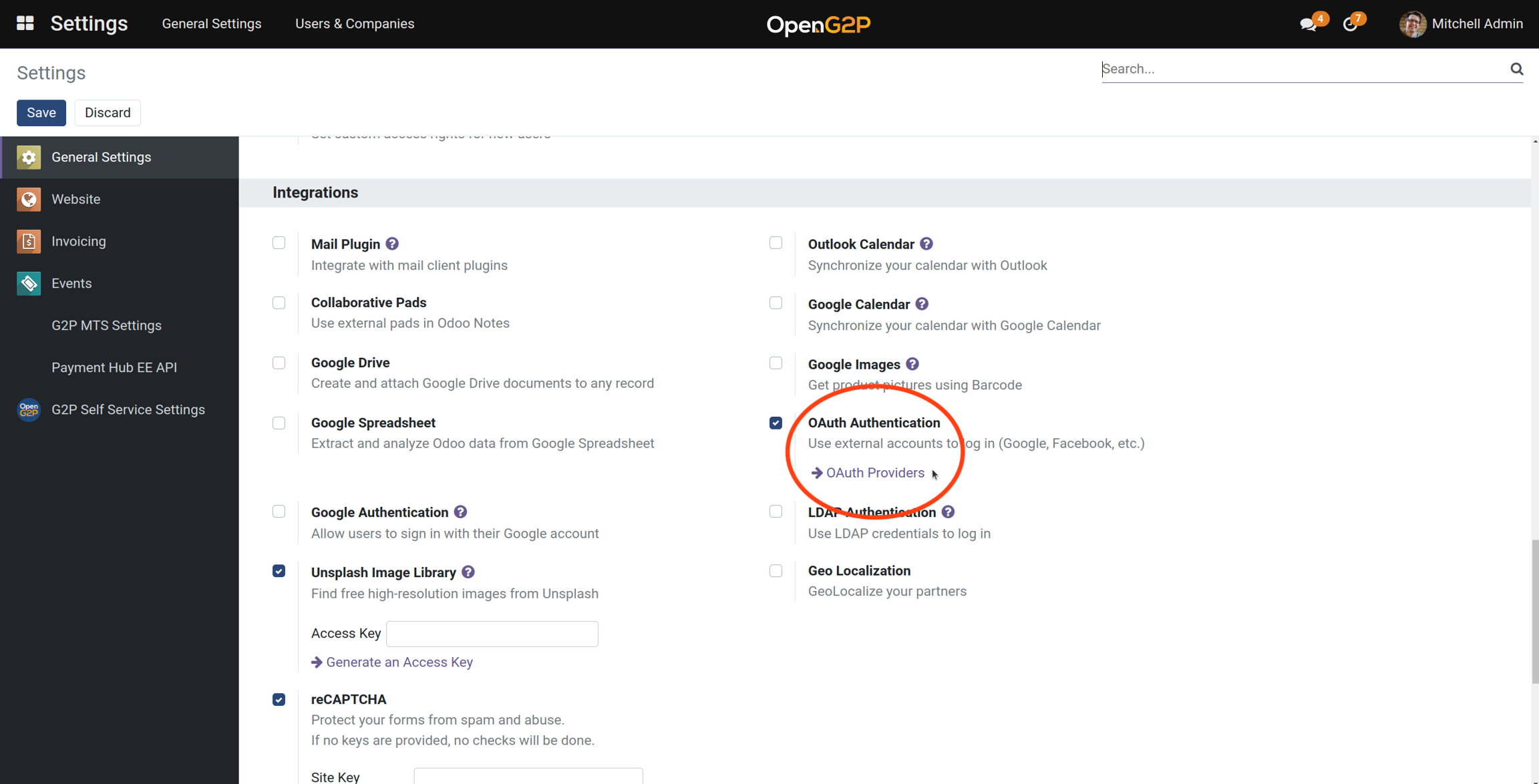
Enable e-Signet on OpenG2P
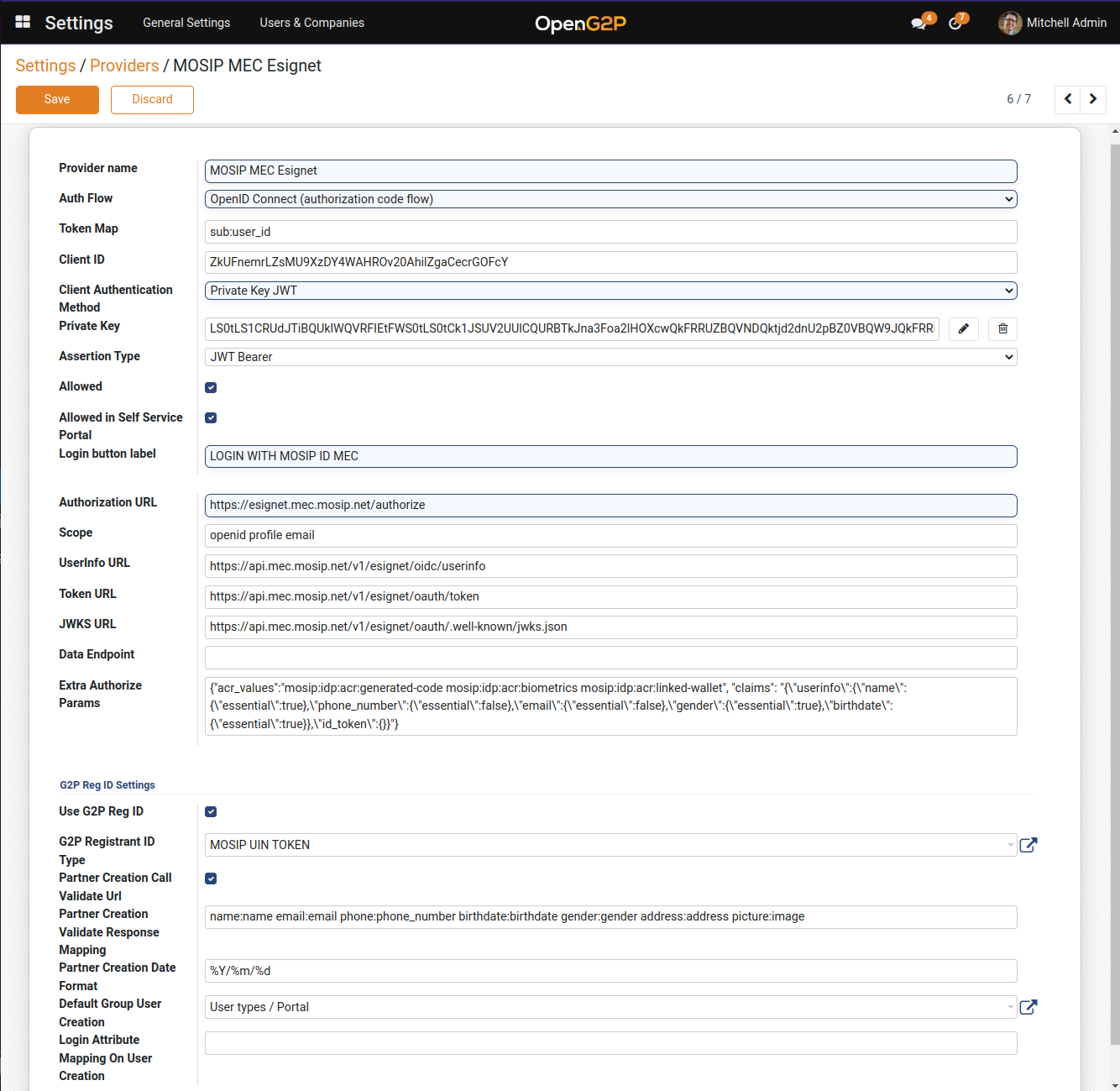
Parameter
Value
Last updated

